Configure SN1PER for Automated OSINT Passive Reconnaissance.
Sn1per is a platform that utilizes many open sourced tools and automates the execution and flags based off the MODE and agruments passed. Sn1per can preform task from light discovery to aggressive RECON and brute forcing. I wanted to utilize it for OSINT Passive Reconnaissance however ran into a few obstacles but was able to iron them out with no trouble.
According to documentation ‘sniper -t
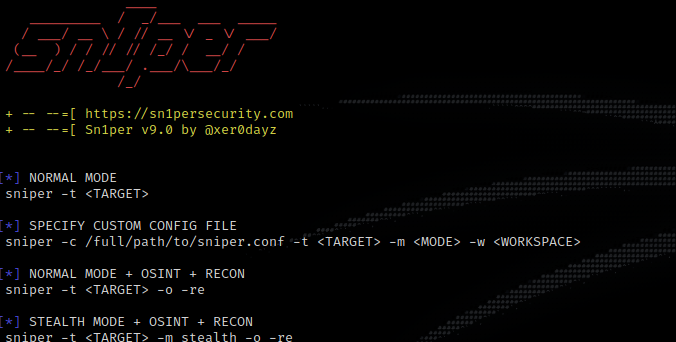
However after running this command on my own domain I found events in my IDS for:
- Port Scanning
- Vulnerablity Scanning
- Command as well as SQL Injection attempts
- LFI attempts
Not my definition of Passive Recon! Which is why its always good to test beforehand.
I noticed the option to specify a custom config file and decided this was the route to take. It took a few times of modifying the config file and running until I was able to weed out all the tools and or functions that communicated directly with the target. Below is the resulting custom config file.
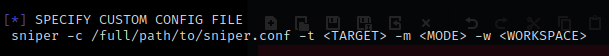
Note That
- The default sniper.conf is located in /usr/share/sniper/sniper.conf
- To run this Specify: sniper -c /full/path/to/configfilename.conf -t thetargetdomain.com -m stealth -o -re
- Don’t forget to add your API keys. More API keys = more data
- Yes Maltego would be the better and ideal option for passive open-source intelligence gathering
cat /usr/share/sniper/sniperPASSIVE.conf
INSTALL_DIR=”/usr/share/sniper” SNIPER_PRO=$INSTALL_DIR/pro.sh PLUGINS_DIR=”$INSTALL_DIR/plugins”
#COLORS OKBLUE=’\033[94m’ OKRED=’\033[91m’ OKGREEN=’\033[92m’ OKORANGE=’\033[93m’ RESET=’\e[0m’ REGEX=’^[0-9]+$’
#AUX MODE OVERRIDE #AUTO_BRUTE=”0” #FULLNMAPSCAN=”0” #OSINT=”0” VULNSCAN=”0”
#DEFAULT SETTINGS ENABLE_AUTO_UPDATES=”1” REPORT=”1” LOOT=”1”
#OUT OF SCOPE OUT_OF_SCOPE=(“www.sn1persecurity.com” “sn1persecurity.com” “*.sn1persecurity.com”)
#SN1PER PROFESSIONAL SETTINGS SNIPER_PRO_CONSOLE_OUTPUT=”0” SN1PER_AUTOLOAD=”0” MAX_HOSTS=”2000”
#DEFAULT BROWSER BROWSER=”firefox”
#BURP 2.0 SCANNER CONFIG BURP_HOST=”127.0.0.1” BURP_PORT=”1338”
#OPENVAS CONFIG OPENVAS=”0” OPENVAS_HOST=”127.0.0.1” OPENVAS_PORT=”9390” OPENVAS_USERNAME=”admin” OPENVAS_PASSWORD=”” OPENVAS_RUNAS_USER=”kali”
#NESSUS CONFIG NESSUS=”0” NESSUS_HOST=”127.0.0.1:8834” NESSUS_USERNAME=”admin” NESSUS_PASSWORD=”” NESSUS_POLICY_ID=”c3cbcd46-329f-a9ed-1077-554f8c2af33d0d44f09d736969bf”
#METASPLOIT SCANNER CONFIG METASPLOIT_IMPORT=”0” MSF_LHOST=”127.0.0.1” MSF_LPORT=”4444”
#SHODAN API KEY SHODAN_API_KEY=””
#CENSYS API KEYS CENSYS_APP_ID=”” CENSYS_API_SECRET=””
#HUNTER.IO API KEY HUNTERIO_KEY=””
#GITHUB API KEY GITHUB_API_KEY=””
#WPSCAN API KEY WP_API_KEY=””
#SLACK API SLACK_NOTIFICATIONS=”0” SLACK_NOTIFICATIONS_THEHARVESTER=”0” SLACK_NOTIFICATIONS_EMAIL_SECURITY=”0” SLACK_NOTIFICATIONS_DOMAINS_NEW=”0” SLACK_NOTIFICATIONS_TAKEOVERS_NEW=”0” SLACK_NOTIFICATIONS_SUBOVER_NEW=”0” SLACK_NOTIFICATIONS_SUBJACK_NEW=”0” SLACK_NOTIFICATIONS_S3_BUCKETS=”0” SLACK_NOTIFICATIONS_SUBNETS=”0” SLACK_NOTIFICATIONS_DIRSEARCH_NEW=”0” SLACK_NOTIFICATIONS_SPIDER_NEW=”0” SLACK_NOTIFICATIONS_WHATWEB=”0” SLACK_NOTIFICATIONS_NMAP=”0” SLACK_NOTIFICATIONS_NMAP_DIFF=”0” SLACK_NOTIFICATIONS_BRUTEFORCE=”0” SLACK_NOTIFICATIONS_WHOIS=”0” SLACK_NOTIFICATIONS_METAGOOFIL=”0” SLACK_NOTIFICATIONS_ARACHNI_SCAN=”0” SLACK_NOTIFICATIONS_EMAIL_FORMAT=”0”
#ACTIVE WEB BRUTE FORCE STAGES WEB_BRUTE_STEALTHSCAN=”0” WEB_BRUTE_COMMONSCAN=”0” WEB_BRUTE_FULLSCAN=”0” WEB_BRUTE_EXPLOITSCAN=”0” WEB_JAVASCRIPT_ANALYSIS=”0” MAX_JAVASCRIPT_FILES=”25”
#WEB BRUTE FORCE WORDLISTS WEB_BRUTE_STEALTH=”$INSTALL_DIR/wordlists/web-brute-stealth.txt” WEB_BRUTE_COMMON=”$INSTALL_DIR/wordlists/web-brute-common.txt” WEB_BRUTE_FULL=”$INSTALL_DIR/wordlists/web-brute-full.txt” WEB_BRUTE_EXPLOITS=”$INSTALL_DIR/wordlists/web-brute-exploits.txt” WEB_BRUTE_EXTENSIONS=”htm,html,asp,aspx,php,jsp,js” WEB_BRUTE_EXCLUDE_CODES=”400,403,404,405,406,429,500,502,503,504”
#GREP PATTERNS STATIC_GREP_SEARCH=”1” GREP_MAX_LINES=”10” GREP_INTERESTING_SUBDOMAINS=”admin|jenkins|test|proxy|stage|test|dev|devops|staff|db|qa|internal” GREP_EXTENSIONS=”.action|.adr|.ascx|.asmx|.axd|.backup|.bak|.bkf|.bkp|.bok|.achee|.cfg|.cfm|.cgi|.cnf|.conf|.config|.crt|.csr|.csv|.dat|.doc|.docx|.eml|.env|.exe|.gz|.ica|.inf|.ini|.java|.json|.key|.log|.lst|.mai|.mbox|.mbx|.md|.mdb|.nsf|.old|.ora|.pac|.passwd|.pcf|.pdf|.pem|.pgp|.pl| plist|.pwd|.rdp|.reg|.rtf|.skr|.sql|.swf|.tpl|.txt|.url|.wml|.xls|.xlsx|.xml|.xsd|.yml” GREP_PARAMETERS=”template=|preview=|id=|view=|activity=|name=|content=|redirect=|(&|[?])access(&|=)|(&|[?])admin(&|=)|(&|[?])dbg(&|=)|(&|[?])debug(&|=)|(&|[?])edit(&|=)|(&|[?])grant(&|=)|(&|[?])test(&|=)|(&|[?])alter(&|=)|(&|[?])clone(&|=)|(&|[?])create(&|=)|(&|[?])delete(&|=)|(&|[?])disable(&|=)|(&|[?])enable(&|=)|(&|[?])exec(&|=)|(&|[?])execute(&|=)|(&|[?])load(&|=)|(&|[?])make(&|=)|(&|[?])modify(&|=)|(&|[?])rename(&|=)|(&|[?])reset(&|=)|(&|[?])shell(&|=)|(&|[?])toggle(&|=)|(&|[?])adm(&|=)|(&|[?])root(&|=)|(&|[?])cfg(&|=)|(&|[?])dest(&|=)|(&|[?])redirect(&|=)|(&|[?])uri(&|=)|(&|[?])path(&|=)|(&|[?])continue(&|=)|(&|[?])url(&|=)|(&|[?])window(&|=)|(&|[?])next(&|=)|(&|[?])data(&|=)|(&|[?])reference(&|=)|(&|[?])site(&|=)|(&|[?])html(&|=)|(&|[?])val(&|=)|(&|[?])validate(&|=)|(&|[?])domain(&|=)|(&|[?])callback(&|=)|(&|[?])return(&|=)|(&|[?])feed(&|=)|(&|[?])host(&|=)|(&|[?])port(&|=)|(&|[?])to(&|=)|(&|[?])out(&|=)|(&|[?])view(&|=)|(&|[?])dir(&|=)|(&|[?])show(&|=)|(&|[?])navigation(&|=)|(&|[?])open(&|=)|(&|[?])file(&|=)|(&|[?])document(&|=)|(&|[?])folder(&|=)|(&|[?])pg(&|=)|(&|[?])php_path(&|=)|(&|[?])style(&|=)|(&|[?])doc(&|=)|(&|[?])img(&|=)|(&|[?])filename(&|=)|id=|select=|report=|role=|update=|query=|user=|name=|sort=|where=|search=|params=|process=|row=|view=|table=|from=|sel=|results=|sleep=|fetch=|order=|keyword=|column=|field=|delete=|string=|number=|filter=|(&|[?])callback=|(&|[?])cgi-bin/redirect.cgi|(&|[?])checkout=|(&|[?])checkout_url=|(&|[?])continue=|(&|[?])data=|(&|[?])dest=|(&|[?])destination=|(&|[?])dir=|(&|[?])domain=|(&|[?])feed=|(&|[?])file=|(&|[?])file_name=|(&|[?])file_url=|(&|[?])folder=|(&|[?])folder_url=|(&|[?])forward=|(&|[?])from_url=|(&|[?])go=|(&|[?])goto=|(&|[?])host=|(&|[?])html=|(&|[?])image_url=|(&|[?])img_url=|(&|[?])load_file=|(&|[?])load_url=|(&|[?])login_url=|(&|[?])logout=|(&|[?])navigation=|(&|[?])next=|(&|[?])next_page=|(&|[?])Open=|(&|[?])out=|(&|[?])page_url=|(&|[?])path=|(&|[?])port=|(&|[?])redir=|(&|[?])redirect=|(&|[?])redirect_to=|(&|[?])redirect_uri=|(&|[?])redirect_url=|(&|[?])reference=|(&|[?])return=|(&|[?])return_path=|(&|[?])return_to=|(&|[?])returnTo=|(&|[?])return_url=|(&|[?])rt=|(&|[?])rurl=|(&|[?])show=|(&|[?])site=|(&|[?])target=|(&|[?])to=|(&|[?])uri=|(&|[?])url=|(&|[?])val=|(&|[?])validate=|(&|[?])view=|(&|[?])window=|daemon=|upload=|dir=|execute=|download=|log=|ip=|cli=|cmd=|file=|document=|folder=|root=|path=|pg=|style=|pdf=|template=|php_path=|doc=|page=|name=|id=|user=|account=|number=|order=|no=|doc=|key=|email=|group=|profile=|edit=|report=|access=|admin=|dbg=|debug=|edit=|grant=|test=|alter=|clone=|create=|delete=|disable=|enable=|exec=|execute=|load=|make=|modify=|rename=|reset=|shell=|toggle=|adm=|root=|cfg=|config=” GREP_XSS=”q=|s=|search=|lang=|keyword=|query=|page=|keywords=|year=|view=|email=|type=|name=|p=|callback=|jsonp=|api_key=|api=|password=|email=|emailto=|token=|username=|csrf_token=|unsubscribe_token=|id=|item=|page_id=|month=|immagine=|list_type=|url=|terms=|categoryid=|key=|l=|begindate=|enddate=” GREP_SSRF=”access|admin|dbg|debug|edit|grant|test|alter|clone|create|delete|disable|enable|exec|execute|load|make|modify|rename|reset|shell|toggle|adm|root|cfg|dest|redirect|uri|path|continue|url|window|next|data|reference|site|html|val|validate|domain|callback|return|page|feed|host|port|to|out|view|dir|show|navigation|open” GREP_REDIRECT=”forward=|dest=|redirect=|uri=|path=|continue=|url=|window=|to=|out=|view=|dir=|show=|navigation=|Open=|file=|val=|validate=|domain=|callback=|return=|page=|feed=|host=|port=|next=|data=|reference=|site=|html=” GREP_RCE=”daemon|upload|dir|execute|download|log|ip|cli|cmd” GREP_IDOR=”id|user|account|number|order|no|doc|key|email|group|profile|edit|report” GREP_SQL=”id|select|report|role|update|query|user|name|sort|where|search|params|process|row|view|table|from|sel|results|sleep|fetch|order|keyword|column|field|delete|string|number|filter” GREP_LFI=”file|document|folder|root|path|pg|style|pdf|template|php_path|doc” GREP_SSTI=”template|preview|id|view|activity|name|content|redirect” GREP_DEBUG=”access|admin|dbg|debug|edit|grant|test|alter|clone|create|delete|disable|enable|exec|execute|load|make|modify|rename|reset|shell|toggle|adm|root|cfg|config”
#DOMAIN WORDLISTS DOMAINS_QUICK=”$INSTALL_DIR/wordlists/domains-quick.txt” DOMAINS_DEFAULT=”$INSTALL_DIR/wordlists/domains-default.txt” #DOMAINS_FULL=”$INSTALL_DIR/wordlists/domains-all.txt”
#DEFAULT USER/PASS WORDLISTS USER_FILE=”/usr/share/brutex/wordlists/simple-users.txt” PASS_FILE=”/usr/share/brutex/wordlists/password.lst” DNS_FILE=”/usr/share/brutex/wordlists/namelist.txt”
#TOOL DIRECTORIES SAMRDUMP=”$INSTALL_DIR/bin/samrdump.py” INURLBR=”$INSTALL_DIR/bin/inurlbr.php”
#FLYOVER MODE TUNING FLYOVER_MAX_HOSTS=”5” FLYOVER_DELAY=”10”
#NMAP OPTIONS NMAP_OPTIONS=”0”
#NETWORK PLUGINS NMAP_SCRIPTS=”0” METASPLOIT_EXPLOIT=”0” MSF_LEGACY_WEB_EXPLOITS=”0” SSH_AUDIT=”0” SSH_ENUM=”0” LIBSSH_BYPASS=”0” SMTP_USER_ENUM=”0” FINGER_TOOL=”0” SHOW_MOUNT=”0” RPC_INFO=”0” SMB_ENUM=”0” AMAP=”0”
#OSINT PLUGINS WHOIS=”1” GOOHAK=”1” INURLBR=”1” THEHARVESTER=”1” METAGOOFIL=”1” HUNTERIO=”0” INTODNS=”1” EMAILFORMAT=”1” ULTRATOOLS=”1” URLCRAZY=”1” VHOSTS=”0” H8MAIL=”0” GITHUB_SECRETS=”0” URLSCANIO=”1”
#DYNAMIC APPLICATION SCANNERS BURP_SCAN=”0” ARACHNI_SCAN=”0” ZAP_SCAN=”0”
#ACTIVE WEB PLUGINS SC0PE_VULNERABLITY_SCANNER=”0” NUCLEI=”0” DIRSEARCH=”0” GOBUSTER=”0” NIKTO=”0” BLACKWIDOW=”0” INJECTX=”0” CLUSTERD=”0” WPSCAN=”0” CMSMAP=”0” WAFWOOF=”0” WHATWEB=”0” WIG=”0” SHOCKER=”0” JEXBOSS=”0” WEBTECH=”0” SSL_INSECURE=”0” HTTP_PROBE=”0” SMUGGLER=”0”
#PASSIVE WEB PLUGINS WAYBACKMACHINE=”1” SSL=”1” PASSIVE_SPIDER=”0” GUA=”1” HACKERTARGET=”1” CUTYCAPT=”0” WEBSCREENSHOT=”0”
#EMAIL PLUGINS SPOOF_CHECK=”1”
#RECON PLUGINS SUBHIJACK_CHECK=”0” AQUATONE=”0” SLURP=”0” SUBLIST3R=”0” AMASS=”0” SUBFINDER=”0” DNSCAN=”0” CRTSH=”0” SUBOVER=”0” PROJECT_SONAR=”1” CENSYS_SUBDOMAINS=”0” SUBNET_RETRIEVAL=”1” SUBJACK=”0” ALT_DNS=”0” MASS_DNS=”0” DNSGEN=”0” SHODAN=”0” ASN_CHECK=”1” SPYSE=”0” SUBBRUTE_DNS=”0” GITHUB_SUBDOMAINS=”0” RAPIDDNS=”1” SCAN_ALL_DISCOVERED_DOMAINS=”0”